This topic provides information about extending authentication and encryption in your Forefront Unified Access Gateway (UAG) DirectAccess deployment.
- Overview
- Requirements
- Limitations
- Planning steps
Overview
By default traffic between DirectAccess clients and the Forefront UAG DirectAccess server is always authenticated and encrypted. The Forefront UAG DirectAccess server acts as an IPsec gateway, and terminates the IPsec tunnels for the DirectAccess client. Traffic between the Forefront UAG DirectAccess server and intranet resources is neither encrypted nor authenticated. Optionally, you can extend authentication and encryption settings, so the Forefront UAG DirectAccess server forwards client traffic as authenticated and encrypted, to selected internal servers.
The following figure shows an example of default configuration.
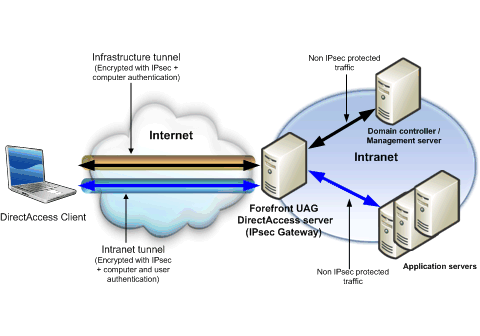
Advantages of the default configuration include the following:
- It does not require IPsec-authenticated traffic in the
enterprise network.
- It allows access to IPv6-capable application servers and
applications on the intranet, in a native IPv6 infrastructure, or
when using ISATAP.
- It allows access to non-IPv6 capable application servers and
applications on the intranet, when using NAT64 and DNS64.
- It enables access to servers that do not support IPsec.
The main disadvantage is that it does not provide authentication or encryption of internal traffic from the Forefront UAG DirectAccess server to the intranet.
The following figure shows an example of extended authentication and encryption.

The main advantages of the extended model is that it provides additional end-to-end authentication, data integrity, and data confidentiality, beyond that provided with traditional VPN connections. The main disadvantages are the operating system requirements, and the need for an IPv6 address.
Requirements
Requirements are as follows:
- The internal servers to which you want to extend IPsec
authentication and encryption must be running Windows Server 2008
or Windows 7.
- The internal servers must have a valid IPv6 address (Native or
ISATAP, not NAT64).
- The servers must be members of one or more AD DS security
groups.
Limitations
- The internal servers must belong to the same forest as the
Forefront UAG server.
- Servers must be accessible over IPv6.
Planning steps
Planning steps include the following:
- Decide whether you require extended authentication and
encryption in your deployment.
- Identify the required internal application servers
- Ensure that the servers are in the required forest and are part
of a security group.





