Forefront Unified Access Gateway (UAG) DirectAccess clients can connect to intranet resources by using two types of IPsec protection access models: end-to-edge and end-to-end.
End-to-edge protection
End-to-edge is the default setting, and refers to the IPsec connection between a DirectAccess client and the DirectAccess server. DirectAccess clients establish an IPsec session to an IPsec gateway server (the Forefront UAG DirectAccess server). The Forefront UAG DirectAccess server then forwards non IPsec-protected traffic to application servers on the intranet. This architecture does not require IPsec on the intranet and works with any IPv6-capable application servers.
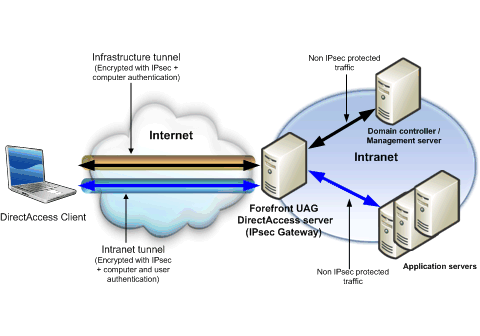
Figure 2 End-to-edge protection
End-to-end protection
End-to-end protection refers to the IPsec connection between a DirectAccess client and application servers on the internal network. End-to-end uses the end-to-edge settings, and in addition extends IPsec policies through to specific application servers. To configure end-to-end protection you specify that DirectAccess should use authenticate traffic between DirectAccess clients and selected application servers. The DirectAccess server forwards the authenticated and IPsec-protected traffic to the specified servers. Optionally, you can select to encrypt the data between the DirectAccess client and application servers, by configuring the IPsec quick mode settings. To use IPsec encryption, application servers must be running Windows Server 2008 or Windows Server 2008 R2, and use both IPsec and IPv6. Note that Intranet application servers not included in Active Directory security groups that use the end-to-end access model are still accessible using the end-to-edge access model.

Figure 3 End-to-end protection
Choosing end-to-edge or end-to-end
Consider the following when deciding which model to use:
- Use end-to-edge protection when you want to
avoid deploying both IPv6 and IPsec throughout your enterprise
network. End-to-edge protection closely resembles VPNs and, as
such, can be more straightforward to deploy.
- For the highest level of security, deploy
IPv6 and IPsec throughout your organization, upgrade application
servers to Windows Server 2008 or
Windows Server 2008 R2, and use end-to-end
protection. With this deploy you can configure end-to-end with
authentication and encryption.





