The Forefront UAG DirectAccess server is a required component of any DirectAccess design. A Forefront UAG DirectAccess server must be running Windows Server 2008 R2.
This topic provides the following information about Forefront UAG DirectAccess server deployment:
- When to install a Forefront
UAG DirectAccess server
- Where to place the Forefront
UAG DirectAccess server
- Planning redundancy for
a Forefront UAG DirectAccess server
When to install a Forefront UAG DirectAccess server
All Forefront UAG DirectAccess designs described in this guide require that you install at least one Forefront UAG DirectAccess server. In some cases, you may deploy a Forefront UAG array and load balance more than one Forefront UAG DirectAccess server, to provide redundancy and increased capacity.
For more information, see the following topics:
Where to place the Forefront UAG DirectAccess server
Because Forefront UAG DirectAccess servers provide intranet connectivity to DirectAccess clients on the Internet, Forefront UAG DirectAccess servers are installed in your perimeter network, typically between your Internet-facing firewall and your intranet. The following figure shows an example.
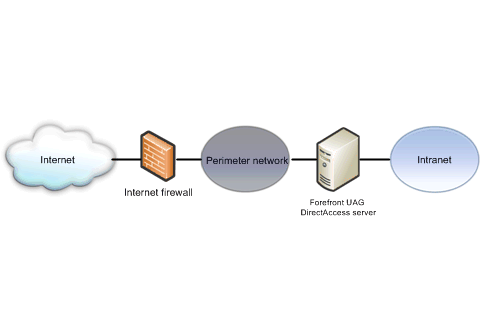
The Forefront UAG DirectAccess server has the following requirements:
- It must be joined to an Active Directory
domain, running Windows Server 2008 R2, and have at least
two physical network adapters installed.
- It must have at least two, consecutive public
Internet Protocol version 4 (IPv4) addresses assigned to the
interface that is connected to the perimeter network, or in the
absence of an Internet firewall, it must be connected directly to
the Internet. Addresses in the ranges 10.0.0.0/8, 172.16.0.0/12,
and 192.168.0.0/16 are private IPv4 addresses and cannot be
used.
- Two consecutive public IPv4 addresses are
required so that the server can act as a Teredo server, and
Windows-based Teredo clients can use the Forefront UAG DirectAccess
server to perform detection of the type of network address
translator (NAT) that they are behind. For more information, see
Teredo Overview
(http://go.microsoft.com/fwlink/?LinkId=169486).
Planning redundancy for a Forefront UAG DirectAccess server
Forefront UAG DirectAccess can be configured to provide service and hardware redundancy, scalability and high-availability, and supports the following methods of load balancing:
- Windows Network Load
Balancing—Forefront UAG integrates NLB functionality provided
by Windows Server 2008 R2, with additional functionality
that enables load balancing of Forefront UAG DirectAccess servers.
Forefront UAG NLB provides load balancing for up to 8 Forefront UAG
DirectAccess array members.
Forefront UAG enables load balancing of SSL based traffic in addition to Forefront UAG DirectAccess based traffic. To load balance all Forefront UAG DirectAccess traffic, which is IPv6 based, Forefront UAG NLB must examine the IPv4 tunneling for all transition technologies. Because IP-HTTPS traffic is encrypted, examining the content of the IPv4 tunnel is not possible (for information on IP-HTTPS, see Connectivity). To enable IP-HTTPS traffic to be load balanced, you must allocate a wide enough IP-HTTPS IPv6 prefix to enable the Forefront UAG to assign a different IPv6 /64 prefix to each of the nodes. For example, 2 array members require a /63 prefix (which enables Forefront UAG to define a /64 address for each array member); 8 array members require a /61 prefix (which enables Forefront UAG to define a /64 address for each array member). This prefix must be routable to the Forefront UAG DirectAccess array, and is configured during the Forefront UAG DirectAccess Configuration. For more information, see Configuring IPv6 prefix addresses.
- External Load Balancing—Forefront UAG
DirectAccess supports the use of external load balancing solutions,
enabling the load balancing of Forefront UAG DirectAccess servers.
For a list of load balancing devices that support Forefront UAG
DirectAccess, see Partners(http://go.microsoft.com/fwlink/?LinkId=166184).





